Often unknown tokens are sent to MetaMask without permission.
They are most often “scan token” to extract funds from Metamask.
Dangerous tokens that are likely to extract all the funds in the connected address, simply by manipulating the token.
What exactly is wrong with metamasks?
There are three key points to note.
- Watch out for Approve.
- Do not connect your metamask to phishing sites
- Don’t get carried away if a price is attached
Also, how to recognise fraudulent tokens and how to combat fraud in metamasks.
- Metamask revoke permissions
- Separate addresses for use
- Search for tokens on Twitter
These are three.
I will now discuss them in detail.
Watch out for Approve
What exactly can be done to get funds pulled out of Metamask?
Approve token
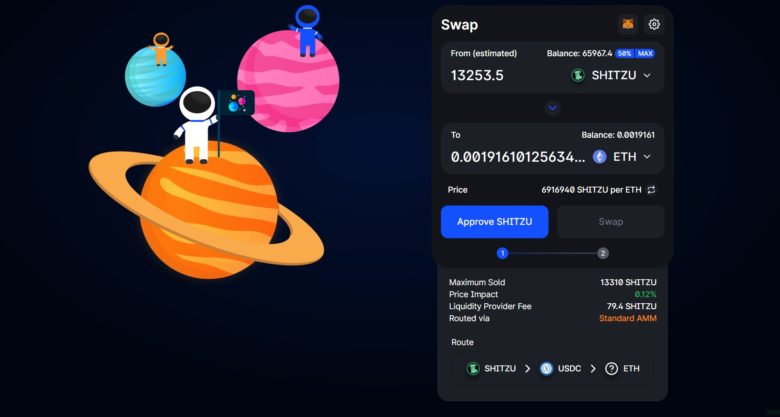
*SHITZU is not a scam token.
As shown in the image, when you swap tokens, you press the button Approve and then press the button Swap to swap tokens.
Approve and allow Metamask to manipulate this token
The programme in the fraud token is triggered and all other assets stored in the MetaMask are extracted.
And the extracted tokens are 100% non-returnable.
Do not connect your metamask to phishing sites
If you receive a token, you’ll want to check it out
And if you get to the website of the project issuing the token
Never connect your metamask.
This connection (wallet connect) alone is dangerous, as the funds in the metamask can be extracted.
Don’t get carried away if a price is attached
It is also dangerous if the coin resembles the name of a well-known coin that everyone knows.
If you try to swap them without checking them carefully, you risk losing all of your MetaMask funds if they are fraudulent tokens.
If it is a fraudulent token, all your MetaMask funds will be taken out.
Note that they are made to state high prices
This is a trap to get people to exchange their tokens for other tokens.
When you have these overpriced tokens in your wallet.
Your assets are growing! Yes! It’s easy to think, “But, stay calm!
Priced tokens don’t just rain down on you without you doing anything.
If you don’t touch them, nothing will happen, so ignore them.
Metamask revoke permissions
With the metamask setting, you can see the sites you have connected to before
If you have connected to a suspicious site or have forgotten that you were previously connected
You can use this setting to disconnect.
This is called Revoke.
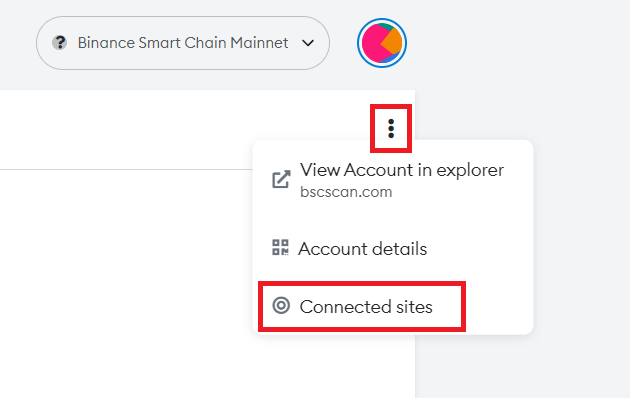
First click on the three dots in the top right corner of the metamask
Click on the connected site
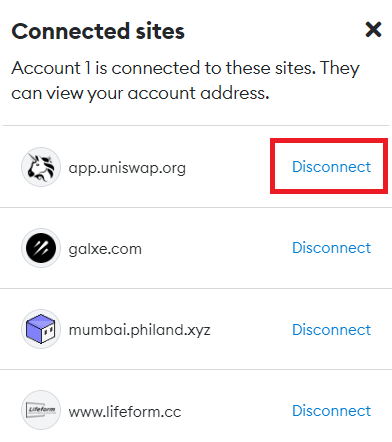
You will then see a list of the sites you have connected to so far and press Disconnect to revoke the connection!
Separate addresses for use
You can spread the risk by using a main address and a sub-address.
If you use a sub-address, such as when applying for tokens or NFT Giveaways (airdrops), which are often done on Twitter, you can be safe even if you receive scam tokens.
For more information on how to create a sub-address with a meta-mask, see this article.
Search for tokens on Twitter
Search for the sent token in the Twitter search window
$〇〇〇 lang:ja
Enter the symbol of the token in the ‘〇’ part of the search.
The lang:ja part means that only tweets in Japanese will be searched.
In most cases, people who have been sent tokens that they don’t know in the same meta mask will tweet to alert you to the token.
In most cases, people who have been sent tokens that they don’t know have tweeted a warning, so this is a good place to start.
Conclusion
These were the steps to take if you receive an unknown token.
It is very important to take measures to avoid being scammed using these methods.
Enjoy the world of crypto currency, where scams are common, with a high level of defence.

